checking uncoverd part of websecurity
Discover and Address Every Vulnerability with Vulncure's Precision Web Pentesting.
Boost your website’s security effortlessly! With Vulncure’s Precision Web Pentesting, we find and fix every vulnerability, ensuring your online space is safe and sound. Trust us for straightforward, effective protection against cyber threats.

The Right Security Partner Safeguards Your Progress and Reputation
Ensuring the security of your business, meeting international standards, and establishing a trusted brand are essential in today’s digital landscape.
– Your security needs are unique. The right partner tailors security solutions to fit your specific requirements, providing a customized approach that aligns with your business objectives.
– A comprehensive pentest is the logical next step to identify and eliminate all vulnerabilities.
– However, selecting the right security partner is crucial to safeguard your progress and protect the hard-earned reputation you’ve built.
Your Technology & Our Expertise










Uncover the Secrets of Web App Pentesting: Step By Step
Preparation and Planning:
- Clearly define the scope of the test, including which web applications and components will be tested.
- Establish the objectives of the penetration test, such as identifying vulnerabilities, ensuring compliance with security standards, or testing specific functionalities.
Gather Information:
- Collect information about the web application, its architecture, technologies, and potential entry points.
- Enumerate all URLs, endpoints, and inputs that need to be tested.
Threat Modeling:
- Identify potential threats and attack vectors that could target the web application.
- Consider common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and authentication issues.
Scanning and Enumeration:
- Use automated tools like web vulnerability scanners to discover common vulnerabilities.
- Manually enumerate the application to identify potential security issues.
Vulnerability Assessment:
- Analyze the results of the scans to determine which vulnerabilities are present.
- Prioritize vulnerabilities based on their severity and potential impact.
Manual Testing:
- Perform manual testing to identify vulnerabilities that automated tools may miss.
- This includes testing for business logic flaws, session management issues, and authentication vulnerabilities.
Exploitation:
- Attempt to exploit identified vulnerabilities to confirm their validity and assess the level of risk.
- We always obtain proper authorization before attempting any exploitation.
Reporting:
- Document all identified vulnerabilities, including their severity, impact, and recommendations for mitigation.
- Provide clear and concise reports that can be understood by technical and non-technical stakeholders.
Re-Testing:
- After fixes are applied, conduct a re-test to ensure that vulnerabilities have been properly addressed.
- Verify that no new vulnerabilities have been introduced during the remediation process.
Final Report:
- Create a final report that includes the results of the re-testing phase and confirms that the vulnerabilities have been resolved.
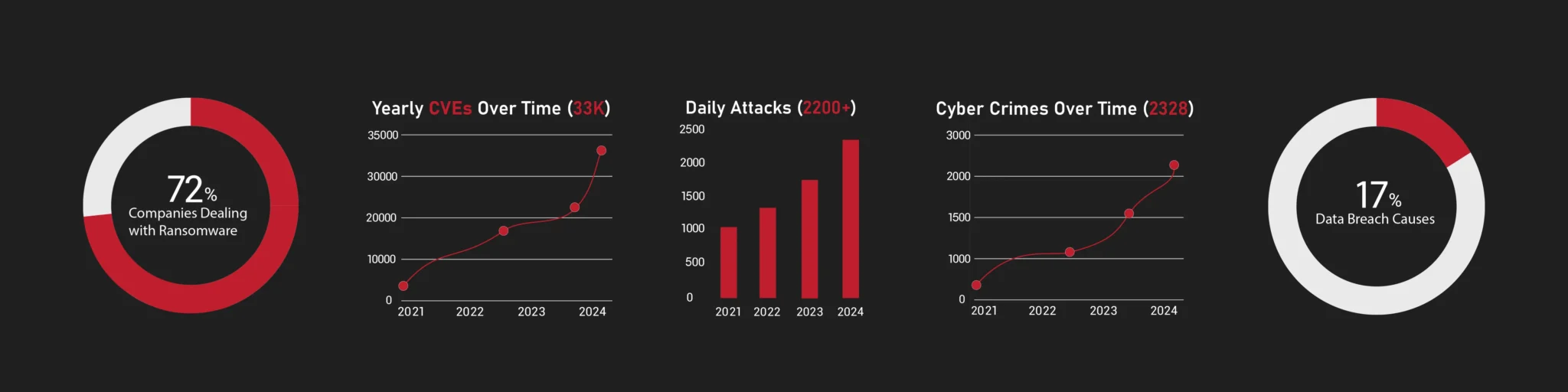
Let’s talk about your Assets
Ready to connect? Take the next step by clicking the button below to schedule a personalized meeting with us. We look forward to connecting with you.