In our hyper-connected digital world, cyber threats loom large over organizations across every industry. From small startups to multinational conglomerates, any entity with an online footprint is a potential target for malicious actors hell-bent on exploiting vulnerabilities for nefarious gain. This alarming reality underscores the critical importance of penetration testing – a proactive cybersecurity measure that simulates real-world attacks to identify and remediate weaknesses before criminals can take advantage.
At its core, penetration testing (often abbreviated as pen testing) involves ethical hackers or security experts attempting to breach an organization’s defenses in a controlled manner. By emulating the tactics and techniques of real cyber criminals, these white-hat hackers relentlessly probe networks, applications, devices, and processes to pinpoint gaps in security protocols. Their efforts illuminate an honest assessment of vulnerabilities that could be exploited to devastating effect if left unaddressed.
“If you don’t have someone actively attempting to tear down your security barriers, you won’t know where the weaknesses are.”
What are the benefits of getting a penetration test?
Here are the key benefits of penetration testing for organizations, presented in point form:
-
- Vulnerability Identification – Pen tests proactively uncover vulnerabilities that automated scans may miss, allowing organizations to remediate gaps before real attackers exploit them.
-
- Objective Security Assessment – Ethical hackers provide an unbiased, real-world evaluation of an organization’s cybersecurity posture from an offensive mindset.
-
- Evolving Threat Modeling – Penetration tests continuously evolve tactics to mirror emerging hacker techniques, helping organizations stay ahead of new attack vectors.
-
- Defensive Validation – By attempting to circumvent security controls, pen tests validate whether preventative measures will effectively thwart skilled criminal efforts.
-
- Regulatory Compliance Assurance – Many industries and governance bodies mandate third-party penetration testing to verify baseline security standards are upheld.
-
- Incident Response Readiness – Simulating attacks allows security teams to pressure-test detection and incident response capabilities against realistic breach scenarios.
-
- Continuous Improvement – Findings illuminate both vulnerabilities requiring remediation as well as effective defensive practices to reinforce and build upon.
-
- Attacker Perspective – Pen testers think and act like real-world hackers, providing unique insights into how criminals view and attempt to infiltrate the organization.
-
- Cost Justification – The potential financial losses from a successful cyber attack far outweigh the investment in proactive penetration testing engagements.
By employing the attacker mindset against themselves in a controlled manner, organizations can honestly evaluate and continuously improve their cyber resilience before threats become crippling realities.
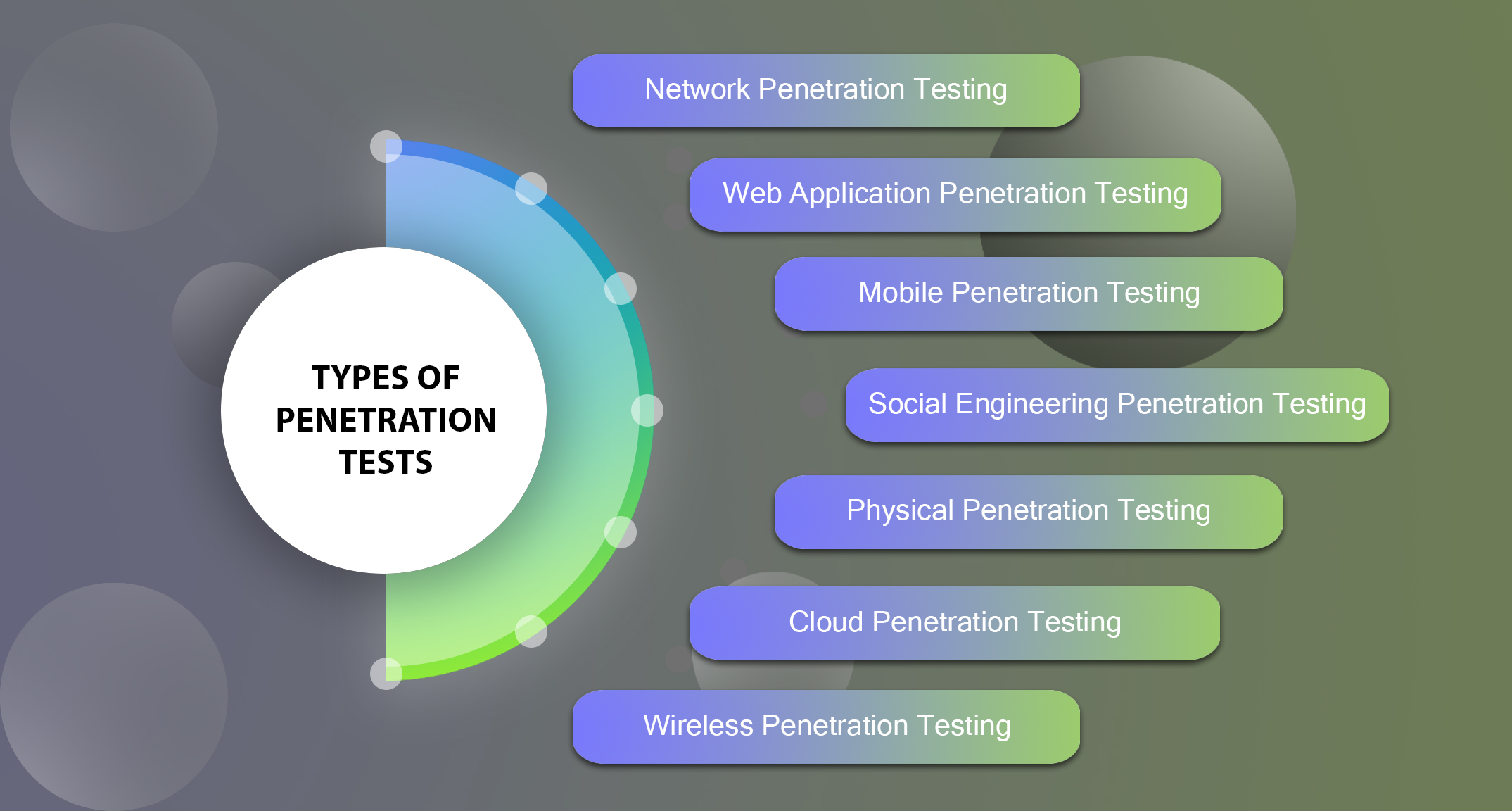
Types of Penetration Tests
However, penetration testing is not a one-size-fits-all approach; there are various types of pen tests tailored to address different objectives and targets. In this article, we’ll explore the most common types of penetration testing and their respective purposes.
-
- Network Penetration Testing: Network penetration testing focuses on evaluating the security of an organization’s network infrastructure, including firewalls, routers, switches, and wireless access points. The primary goal is to identify vulnerabilities that could allow unauthorized access or lateral movement within the network. This type of testing can be further subdivided into external and internal network pen tests.
- Web Application Penetration Testing: With the increasing reliance on web-based applications, web application penetration testing has become crucial. This type of testing aims to uncover vulnerabilities in web applications, such as cross-site scripting (XSS), SQL injection, and insecure authentication or authorization mechanisms. By exploiting these vulnerabilities, pen testers can assess the potential impact on the confidentiality, integrity, and availability of the application and its underlying data.
- Mobile Application Penetration Testing: As mobile devices and applications become more prevalent, mobile application penetration testing has emerged as a specialized area. This testing involves assessing the security of mobile apps, including their communication channels, data storage practices, and potential vulnerabilities in the underlying mobile operating systems.
- Social Engineering Penetration Testing: Social engineering attacks exploit human behavior and vulnerabilities rather than technical weaknesses. In this type of pen test, ethical hackers attempt to manipulate individuals into divulging sensitive information or granting unauthorized access through various techniques, such as phishing, pretexting, or physical intrusion.
- Physical Penetration Testing: Physical penetration testing evaluates the security of an organization’s physical premises, including buildings, data centers, and other facilities. Pen testers attempt to gain unauthorized access to restricted areas, test physical security controls, and assess the effectiveness of access control measures and employee awareness.
- Cloud Penetration Testing: As more organizations migrate to cloud environments, cloud penetration testing has become increasingly important. This type of testing focuses on evaluating the security of cloud-based services, infrastructure, and configurations, ensuring that sensitive data and applications hosted in the cloud are adequately protected.
- Wireless Penetration Testing: Wireless penetration testing targets the security of an organization’s wireless networks, including Wi-Fi, Bluetooth, and other wireless communication protocols. Pen testers attempt to gain unauthorized access, intercept wireless transmissions, or exploit vulnerabilities in wireless security protocols.
These are just a few examples of the different types of penetration testing that are available. Organizations may choose to conduct a combination of these tests, depending on their specific requirements, threat landscape, and areas of concern. Regardless of the type, penetration testing remains a vital component of a comprehensive cybersecurity strategy, providing organizations with the insights and knowledge necessary to strengthen their defenses and protect their valuable assets.
You can’t secure what you can’t see. Penetration testing illuminates blind spots in security defenses.
How are penetration tests done?

Here’s an overview of how penetration testing is typically carried out:
-
- Planning and Scoping: The first step involves defining the goals, scope, and rules of engagement for the penetration test. This includes identifying the target systems, networks or applications to be tested, as well as any off-limits areas. The testing team and client agree on the specifics like timelines, deliverables, and permitted attack methods.
- Reconnaissance: Before any exploits are attempted, pen testers gather as much information as possible about the target environment through open-source intelligence (OSINT) and other reconnaissance techniques. This could include website analysis, DNS enumeration, employee profiling on social media, etc. to map out potential attack surfaces.
- Threat Modeling: Based on the data collected, the pen testing team develops a model of potential threat vectors and vulnerabilities that could be present in the target systems. This guides their later exploitation efforts toward the most likely weaknesses.
- Vulnerability Analysis: Testers then switch to an active analysis mode, using port scanning, web app spidering, and other methods to probe for specific vulnerabilities across the target attack surfaces identified earlier. Automated vulnerability scanners may be used in conjunction with manual techniques.
- Exploitation: The core of the pen test occurs when verified vulnerabilities are attempted to be exploited through methods like code injection, social engineering, privilege escalation, etc. Seasoned pen testers get creative in combining vulnerabilities and pivoting between systems.
- Post-Exploitation: If successful in breaching defenses, pen testers then further advance their access by installing backdoors, stealing data, elevating privileges, and emulating the actions of a real-world attacker to demonstrate the potential impacts.
- Analysis and Reporting: Finally, all findings, successful exploits, and recommended remediation steps are compiled into a detailed report for the client. This “proof of exploitation” report serves as a comprehensive assessment of the target’s security posture.
Throughout this process, pen testers rigorously follow their rules of engagement, carefully documenting each step taken while ensuring no unintended damage is caused to production systems. The entire pen test simulates a realistic cyber attack in a controlled and fully consensual way.
How often should you take a pentest?
Here’s a more conversational, human-written take on how often organizations should conduct penetration testing:
There’s no hard and fast rule about how frequently you need to bring in ethical hackers for a full pen testing engagement. It really depends on your organization’s unique circumstances and risk exposures. That said, most cybersecurity professionals recommend making it a regular practice—anything from once every few months to at least annually in most cases.
If your company operates in a high-risk environment dealing with sensitive data, and critical infrastructure, or has been burned by breaches before, you’ll want to be on the more frequent end of that spectrum. Think along the lines of quarterly or bi-annual pen tests. The threats just aren’t letting up in those arenas, so you need continuous validation that your defenses are hardened against the latest tricks.
For more moderate-risk businesses maybe in e-commerce, technology services, consulting etc. – an annual penetration test is generally advisable. It allows you to comprehensively re-assess your security gaps and controls at least once per year as your environment evolves.
But there are also certain event-driven cases where a pen test should be prioritized regardless of your regular cadence. Like if you’re making major system upgrades, launching new code or apps, got acquired, or heaven forbid, suffered an actual incident. Those are pivotal times to re-evaluate your attack surface and make sure no new cracks have opened up.
Some industries have strict requirements too based on compliance regimes. Regulations like PCI-DSS or HIPAA may legally mandate penetration testing at prescribed intervals. For those folks, schedules are set by auditors rather than risk callouts.
The main thing is – you can’t just set it and forget it with security testing. Penetration tests represent your best assessment of how well your defenses would actually stack up against realistic attacks and skilled adversaries. Waiting years between checks is just asking for vulnerabilities to accumulate in the meantime. It should be a continuous, proactive effort aligned with your risk appetite and situation.
When don’t you need a pentest?
There are certain scenarios where organizations may not necessarily need to conduct penetration testing. Here are some situations when penetration testing may not be required or could be postponed:
-
- Early Stages of Development: For applications or systems that are still in the early stages of development and not yet deployed in a production environment, penetration testing may not be immediately necessary. Instead, it’s recommended to focus on secure coding practices, code reviews, and automated security testing during this phase.
- Limited Attack Surface: If an organization has a minimal online presence or a very limited attack surface (e.g., a small internal network with no internet-facing services), the risk of cyber attacks may be lower. In such cases, a comprehensive risk assessment could help determine if penetration testing is warranted or if other security measures are sufficient.
- Recent Penetration Test: If an organization has recently undergone a thorough penetration test and has addressed all identified vulnerabilities, it may not need to conduct another test immediately, unless there have been significant changes to the environment or new assets introduced.
- Limited Resources: For small organizations or startups with limited budgets and resources, the cost of penetration testing may be prohibitive. In such cases, they may opt for more cost-effective security measures, such as vulnerability scanning, secure coding practices, and employee security awareness training.
- Regulatory Compliance: In some industries or regions, penetration testing may not be explicitly required by regulatory bodies or compliance standards. However, it’s important to note that even in these cases, penetration testing can still be beneficial as a proactive security measure.
- Low-Risk Environment: If an organization operates in a low-risk environment with minimal exposure to cyber threats (e.g., a small business with no sensitive data or critical infrastructure), they may choose to focus their security efforts on other areas, such as access control, backups, and incident response planning.
It’s important to note that while these scenarios may not necessitate immediate penetration testing, it’s generally recommended to incorporate penetration testing as part of an overall cybersecurity strategy. Regular testing helps organizations identify and mitigate vulnerabilities proactively, ensuring they are prepared to address evolving cyber threats effectively.
Choosing the Right Pentesting Service Provider:
When selecting a pentesting service provider, it’s crucial to consider factors such as their experience, expertise, certifications, and industry reputation. Look for providers that offer tailored services to meet your organization’s specific needs and adhere to industry best practices and ethical standards.
How we can help?
At Vulncure, we understand the critical importance of maintaining a robust cybersecurity posture in today’s ever-evolving threat landscape. Our team of highly skilled and experienced ethical hackers and security professionals are dedicated to helping organizations like yours identify and mitigate vulnerabilities before they can be exploited by malicious actors.
Our comprehensive penetration testing services are tailored to meet your specific needs and address the unique challenges faced by your industry and organization. We employ a wide range of techniques, including network penetration testing, web application testing, cloud penetration testing, and more, to provide a holistic evaluation of your security defenses.
What sets us apart is our deep understanding of the attacker’s mindset and our ability to think like cybercriminals. Our pentesters are constantly staying up-to-date with the latest hacking techniques, tools, and methodologies, ensuring that we can identify and exploit vulnerabilities that others may miss.
At Vulncure, we believe that a proactive approach to cybersecurity is essential for protecting your organization’s valuable assets, maintaining compliance, and safeguarding your reputation. By leveraging our pentesting services, you can gain confidence in your security posture and take the necessary steps to fortify your defenses against potential threats.”
Feel free to customize and expand on this section to align with your company’s specific offerings, strengths, and value proposition. The key is to highlight your expertise, experience, and commitment to helping clients achieve a robust security posture through comprehensive and effective penetration testing services.
Ready to fortify your defenses with robust pentesting?
Schedule a meet with our cybersecurity experts today. Together, we’ll strengthen your security posture against emerging threats.
Conclusion:
In the ever-evolving landscape of cyber threats, pentesting services play a vital role in helping organizations identify and mitigate vulnerabilities before they can be exploited. By proactively assessing and fortifying their cybersecurity defenses, organizations can better protect their digital assets, maintain compliance, and safeguard their reputation and business continuity.
