In our digital age, cybersecurity threats are escalating in sophistication and prevalence, posing significant risks across industries. Data breaches, financial losses, reputational damage, and regulatory penalties are all potential devastating consequences of cyber attacks. As such, businesses must proactively prioritize regular security assessments and penetration testing.
In the following sections, we’ll delve into the vital benefits, methodologies, and best practices of security assessments and penetration testing. These safeguard your organization’s digital assets against today’s and tomorrow’s escalating cybersecurity challenges.
Understanding Security Assessments and Penetration Testing: Crucial Vulnerability Management Practices
In today’s ever-evolving cybersecurity landscape, organizations must proactively identify and address potential weaknesses in their systems and networks. Two essential practices for effective vulnerability management are security assessments and penetration testing.
What Are Security Assessments?
Security assessments are comprehensive evaluations of an organization’s digital infrastructure, systems, applications, and security controls. These assessments aim to uncover vulnerabilities, security gaps, and areas of non-compliance that could be exploited by threat actors. Through a combination of automated scanning tools and manual testing, security assessments provide a detailed analysis of an organization’s overall security posture.
What Are Penetration Tests (Pentests)?
Penetration testing, or pentesting, takes vulnerability identification a step further by simulating real-world cyber attacks. Ethical hackers, also known as “white hat” hackers, use the same techniques and tools as malicious actors to attempt to gain unauthorized access to an organization’s systems and networks. Pentests provide a realistic evaluation of an organization’s security defenses, helping to identify vulnerabilities that could be exploited in an actual attack.
The Importance of Security Assessments and Pentests
Regular security assessments and penetration testing are crucial for identifying and mitigating vulnerabilities before they can be exploited by cybercriminals. These practices offer numerous benefits, including:
- Proactive Vulnerability Identification: By conducting regular assessments and pentests, organizations can uncover vulnerabilities and weaknesses before they are discovered and exploited by threat actors.
- Compliance and Risk Management: Many industries and regulatory bodies mandate regular security assessments and penetration testing to ensure compliance with data protection and cybersecurity standards, mitigating legal and financial risks.
- Continuous Improvement: The findings from security assessments and pentests provide valuable insights into an organization’s security posture, enabling continuous improvement and the implementation of effective remediation measures.
- Increased Cyber Resilience: By addressing identified vulnerabilities, organizations can strengthen their overall cybersecurity defenses, enhancing their ability to withstand and recover from potential cyber attacks.
Neglecting security assessments and penetration testing in today’s digital world can expose organizations to data breaches, reputation damage, and fines. Prioritizing these practices helps stay ahead of threats, safeguard data, and maintain trust with customers and stakeholders.
The Consequences of Neglecting Security Assessments and Pentests
In the digital age, ignoring security assessments and penetration testing is like leaving your house’s doors wide open for cyber threats.
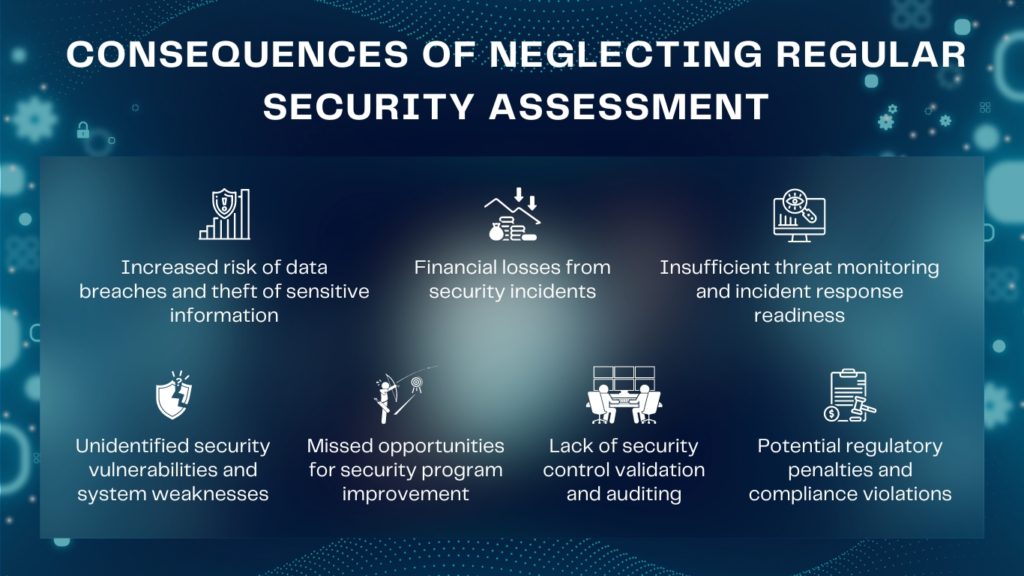
It invites trouble, risking severe consequences for any organization. Let’s take a closer look at the potential fallout:
Data Breaches and Loss of Confidential Information
Neglecting security measures exposes you to the significant risk of a data breach. Picture cybercriminals gaining unauthorized access, stealing customer data, financial records, or trade secrets. More than just privacy violations, breaches trigger costly legal battles and customer mistrust.
It’s analogous to a secret valuables stash at home without locked doors or security systems – an easily exploited vulnerability cybercriminals will eventually discover and target. Proactively securing digital assets through security assessments and penetration testing is crucial to prevent data breaches that jeopardize your most sensitive information and stakeholder relationships.
Financial Losses and Legal Consequences
Data breaches and cyber attacks can have crippling financial implications for organizations, far beyond the immediate costs of incident response and resolution. From regulatory fines and legal fees to long-term brand damage, the expenses rapidly compound.
For instance, companies operating in highly regulated industries like healthcare and finance face hefty penalties for failing to maintain adequate cybersecurity standards. Governing bodies can levy massive fines for non-compliance with data protection regulations.
The financial impact is akin to neglecting routine car maintenance – by skimping on brake repairs, you risk a preventable accident with exorbitant costs for damages, legal battles, and more.
Protecting digital assets requires consistent investment in cybersecurity essentials like vulnerability assessments and penetration testing. These proactive measures identify and remediate weaknesses before threat actors can exploit them, averting catastrophic data breaches.
While upfront cybersecurity spending may seem high, it pales in comparison to the potential fallout from cyber incidents, which can include:
- Breach investigation/recovery costs
- Customer notification expenses
- Regulatory penalties and litigation
- Brand reputation damage and customer churn
- Operational disruption and lost productivity
Neglecting security fundamentals is an enormous risk no organization can afford. Consistent vulnerability management and third-party penetration testing provide a strong return on investment by preventing the steep financial ramifications of cyber attacks.
Damage to Reputation and Customer Trust
One of the most devastating impacts of a data breach is the lasting damage to an organization’s reputation and customer trust. In our hyper-connected world, news of cyber incidents spreads rapidly, tarnishing brand image and equity.
Customers feel betrayed when a company they trusted fails to protect their sensitive data. This breach of trust often leads to customer churn and loyalty erosion, severely impacting the bottom line long-term.
Neglecting security essentials like penetration testing and vulnerability assessments leaves organizations vulnerable to reputation-shattering breaches. It’s a risk no business can afford in today’s threat landscape.
While an investment, prioritizing robust cybersecurity provides priceless insurance – avoiding catastrophic breaches that could irreparably harm the brand. Maintaining customer trust requires proactive measures to secure data.
In summary, the reputational fallout and loss of customer confidence from data breaches are far-reaching and long-lasting. Proactive cybersecurity secures not just data, but protects the very brand equity businesses work so hard to build.
Case Studies
Even large, well-established companies can fall victim to severe data breaches and cyber attacks if they neglect to implement proper security measures. Here are some high-profile case studies that illustrate the consequences of inadequate cybersecurity practices.
Yahoo Data Breaches 2013-2014: When 3 Billion Accounts are Compromised
Between 2013-2014, Yahoo suffered two massive data breaches impacting over 3 billion user accounts – among the largest breaches ever recorded. Outdated encryption, weak authentication processes, and lacking security controls were to blame.

The fallout was immense:
- $350 million discount on Verizon acquisition
- User trust erosion
- Numerous lawsuits and investigations
Equifax Data Breach 2017: When Credit Data is Compromised
Credit reporting agency Equifax failed to patch known software vulnerabilities, leading to a breach that exposed sensitive personal data of 147 million consumers in 2017. Inadequate security controls and incident response measures compounded the issue.

Key impacts of the Equifax data breach include:
- $700 million settlement with FTC and CFPB
- Numerous lawsuits and regulatory investigations
- Plummeting consumer trust and stock value
Benefits of Regular Security Assessments and Pentests
In today’s digital world, where cyber threats are constantly evolving, conducting routine security assessments and penetration tests (a.k.a. pentests) isn’t just a nice-to-have – it’s an absolute necessity. Think of it as getting regular check-ups for your business’s digital well-being, just like you get physical exams to ensure your body is in top shape.
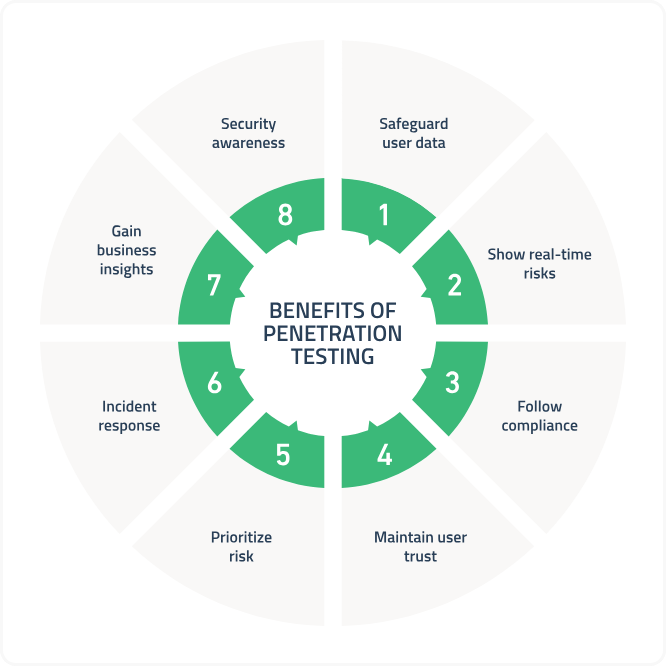
Identification of Vulnerabilities Before They Are Exploited
One of the biggest benefits of regular security assessments and pentests is that they help you identify vulnerabilities before cybercriminals have a chance to exploit them. Imagine being able to spot and fix potential security weaknesses before they become a real problem – it’s like catching a leak in your roof before it leads to a disastrous, costly mess.
Compliance with Regulations and Standards
Many industries and regulatory bodies require businesses to conduct regular security assessments and pentests to maintain compliance with data protection and cybersecurity standards. Failing to meet these requirements can result in costly penalties and legal troubles – a risk no business wants to take.
Cost-Effective Security Measures
While security assessments and pentests may seem like an added expense upfront, they’re actually a cost-effective way to strengthen your cybersecurity defenses. Think about it – the potential financial losses and reputational damage from a data breach or cyber attack can be catastrophic, making routine security check-ups a smart investment in protecting your business.
By prioritizing regular security assessments and pentests, you’re not only safeguarding your digital assets and customer data but also demonstrating your commitment to maintaining a robust cybersecurity posture. It’s like having a team of digital bodyguards constantly on the lookout for potential threats, ensuring your business stays one step ahead of the cyber crooks.
So, don’t wait until it’s too late – make routine security check-ups a top priority for your business. Your future self will thank you.
Conclusion
The consequences of forgoing regular penetration tests are catastrophic – crippling data breaches, steep regulatory penalties, and brand-shattering reputational damage. In our hostile cyber climate, overlooking this critical vulnerability assessment leaves your systems exposed to skilled threat actors.
Don’t blindly leave digital assets vulnerable. Prioritize comprehensive penetration testing by ethical hackers to safely identify exploits before criminals can breach your defenses. Skimping on this essential practice jeopardizes cyber resilience and compliance.
Invest in frequent penetration tests to protect data, finances, and reputation from devastating breaches. Neglecting these assessments is cyber insecurity at its most dangerous. Proactively evaluate your vulnerabilities before attackers infiltrate blindspots. The costs of inaction are far too steep.
References
https://fastercapital.com/startup-topic/Penetration-Testing.html
About me
Hello, I’m Harshi Gupta, a seasoned penetration tester with expertise in both internal and external assessments. Cybersecurity is not just a career path for me; it’s my hobby and passion. With a wealth of experience in identifying and mitigating security vulnerabilities, I am dedicated to ensuring the resilience of organizations’ digital assets. For networking opportunities and engaging discussions, feel free to reach out to me via LinkedIn and Twitter.
