Web App Pentest
Find OWASP Top 10 issues and complex business-logic flaws in your web apps.
- Comprehensive vulnerability scanning
- Business logic testing
- In-depth manual analysis
PTaaS that lets you request tests on demand, see live findings, track remediation and SLAs, and verify fixes with retests—guided by our expert pentesters.
One approach applied across Web, API, Mobile, and Cloud for complete coverage.
Manual + automated testing to find what scanners miss—clear risks and actions.
Find OWASP Top 10 issues and complex business-logic flaws in your web apps.
Secure REST & GraphQL APIs across auth, authz, and data exposure.
Protect iOS/Android from data leakage, insecure storage, and reverse-engineering.
Audit AWS, Azure, and GCP for misconfig, IAM risks, and insecure services.
Find OWASP Top 10 issues and complex business-logic flaws in your web apps.
Secure REST & GraphQL APIs across auth, authz, and data exposure.
Protect iOS/Android from data leakage, insecure storage, and reverse-engineering.
Audit AWS, Azure, and GCP for misconfig, IAM risks, and insecure services.
Schedule a confidential consultation with our specialists to explore how our services can help you secure your digital assets.
and more...
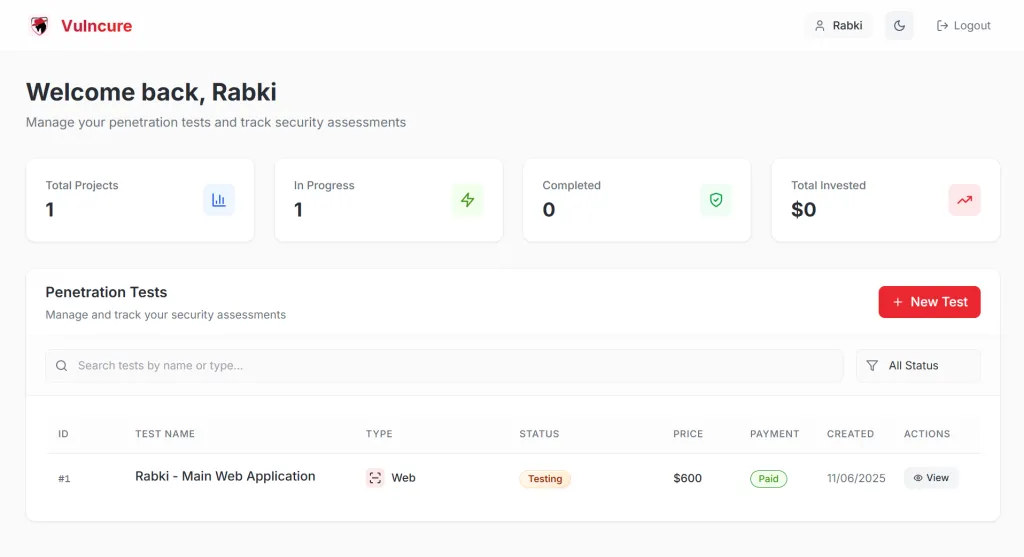
See findings as they’re discovered, track remediation to done, and collaborate with our testers—all in one secure dashboard.
New findings and status changes appear instantly—no waiting for the final report.
At-a-glance view of tests, findings, owners, and SLAs.
Assign owners, prioritize work, and verify fixes with retests.
Get alerts when critical vulnerabilities are discovered during testing.
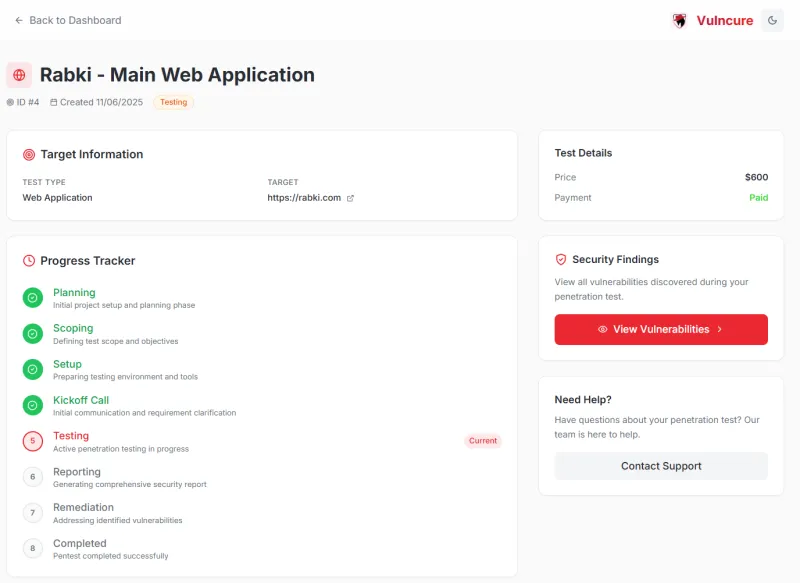
Onboarding
Align goals, timeline, and key contacts to start fast.
Scope & Objectives
Define assets, risks, and priorities for the test.
Environment Setup
Prepare secure access and tooling for testing.
Kickoff & Alignment
Confirm scope, success criteria, and communication.
Active Testing
Simulate real-world attacks to uncover vulnerabilities.
Reporting
Clear risks, repro steps, and remediation guidance.
Remediation Support
Work with your team to fix issues; request retests.
Verified Fixes
Validate fixes and finalize results.
"The pentests results document provided actionable recommendations for enhancing our cybersecurity posture. The comprehensive report was valuable in understanding our security landscape.
We were impressed by the punctuality and professionalism demonstrated in delivery and communication throughout the engagement. Timely updates and responsiveness to queries ensured a smooth collaboration process. The team's commitment to meeting deadlines contributed significantly to our overall satisfaction."
Santosh Usha Srinivasa
Head of Engineering, doctari
About our PTaaS, real-time dashboard, and services
Continuous, expert-led pentesting with real-time visibility and direct support to remediate issues fast.